See all blog posts in this series:
- From VMware to IBM Cloud VPC VSI, part 1: Introduction
- From VMware to IBM Cloud VPC VSI, part 2: VPC network design
- From VMware to IBM Cloud VPC VSI, part 3: Migrating virtual machines
- From VMware to IBM Cloud VPC VSI, part 4: Backup and restore
- From VMware to IBM Cloud VPC VSI, part 5: VPC object model
- From VMware to IBM Cloud VPC VSI, part 6: Disaster recovery
- From VMware to IBM Cloud VPC VSI, part 7: Automation
We interrupt our normal VPC VSI programming to briefly discuss the VPC object model, which is relevant not only to your VPC design and your automation strategy, but also to your backup and especially your DR scenarios. For BCDR, you need to make plans to reconstitute all of these resources. As we have already discussed, it is not sufficient to backup your VSI volumes; you need to be prepared to reconstitute the VSI itself, including details such as the instance profile, IP address, floating IP, and security groups.
Here is my rough attempt to diagram the VPC object model to help you think about your VPC design as well as your BCDR design and planning. Afterwards I will list some caveats.
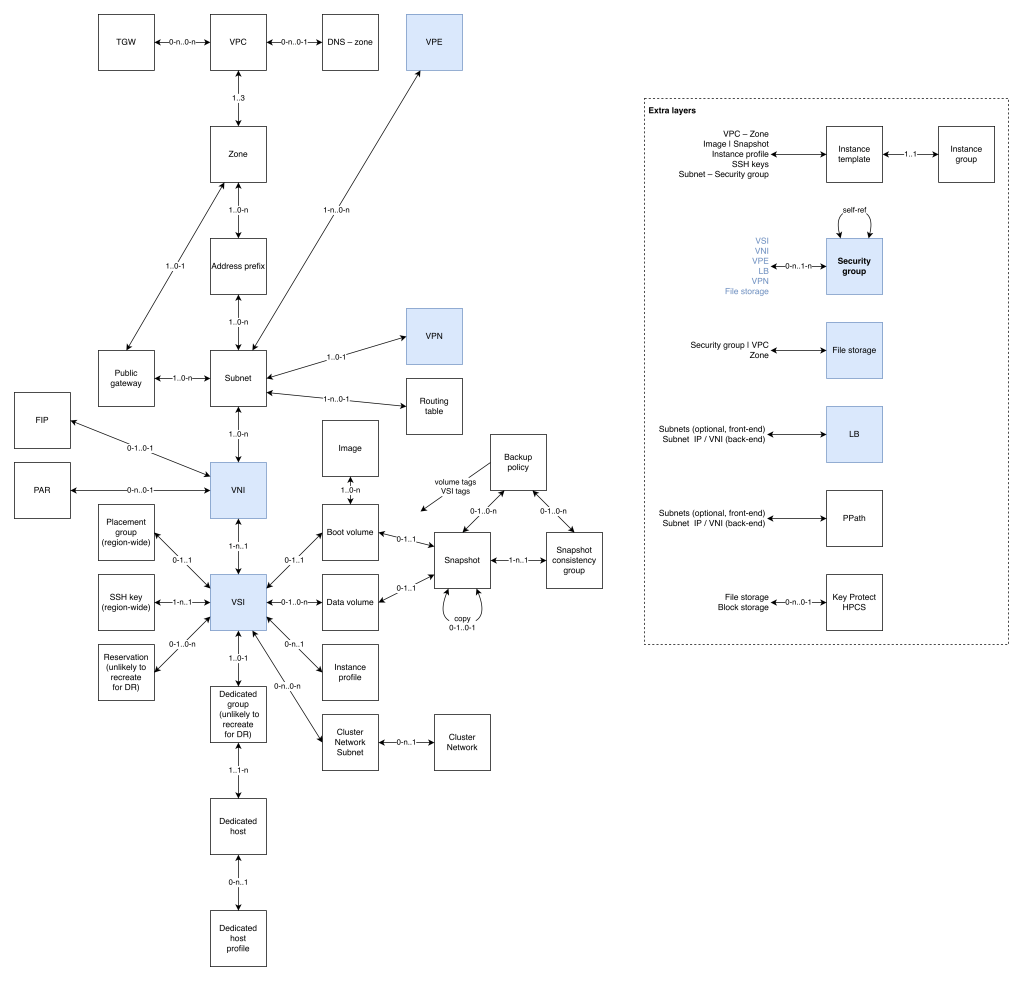
Some resources I have designated by abbreviation (e.g., VPE, LB, FIP, PAR, VNI). I have attempted to specify some cardinality based on my understanding, but it is likely that I have made some mistakes. I’ve also set aside some related resources to the side as a kind of appendix rather than attempting to include them and all of their possible relations in the main diagram. Because the security group impact is so extensive, I have used blue color coding to highlight the extent of its influence.
I’ve included some loosely coupled resources (such as DNS service), but not all such resources (for example, you may be leveraging Cloud Object Storage, IBM Cloud Databases, or Backup and Recovery resources connected through a VPE).
There are other considerations you will need to make such as IBM Cloud IAM permissions; these apply to every single resource. Minimally you need to consider which resource groups each resource is placed in and which users, access groups, and services should have access to them. If you are using the metadata service or allowing your VSIs to access trusted profiles and other resources, you will also need to consider the appropriate IAM configuration for this as well.
You may also need to consider quota and capacity management.